The information contained herein is provided as-is, and has been prepared with a conscious effort to abstain from opinionated language. With that being said, imperfections and inaccuracies are inevitable to a non-zero degree.
If you see something that is inaccurate or incorrect, please reach out to us at contact@shadowfury.xyz or on Twitter, @shadowfury_xyz.
Likewise, if you have information you wish to share, please do so. Information is vital toward our unified goal of prosecuting the threat actors behind these egregious financial crimes.
We are interested in hearing about your encounters; your voice matters.
Lastly: if you are reading this, and you are involved in the act of executing, or aiding in the execution of these crimes ... we see you.
We are watching constantly and we have spoken to you directly on multiple occasions.
We'll keep in touch. / SFS
We have been following along since early September. This will be an account of both recent and more distant events. Our intent is to open discussions and stir interests.
Recently we observed the theft of multiple RTFKT CloneX NFTs. The first transactions follow the sequence/s outlined below.
| Identifier | Reference or ENS | Full Address or TX Hash | Notes |
|---|---|---|---|
| Victim |
be984f
|
0xbe984f5d3D6040d57fFc8d7700243E29dA6750b7
|
|
| Threat actor #1 |
E5E674, cyberprincess.eth
|
0xE5E67488628B689fE046eF24817AeF3FBE9Be033
|
This is not the drainer. |
| Relevant transaction #1 |
94c809
|
0x94c08991b8d18aacc381afab3cafcd2fb29400ac3c15a5989be559a7800952a3
|
0 Ether from be984f to E5E674
|
| Rel. transaction #2 |
0b2c82
|
0x0b2c82f412dbb41090ef61d77082aa1a4943fc73b2e4d4482f1ac760473cf0ea
|
0 Ether from be984f to E5E674
|
| Rel. transaction #3 |
7909c0
|
0x7909c03629dc002d86f686252cef66e8322facb60cce56222a00e9368af598a2
|
0 Ether from be984f to E5E674
|
| First transfer of value (#4) |
b22baf
|
0xb22bafff29908031ca787318511a0ac020f97668c0994178252d59d2833ae343
|
4.15 Ether ($4,517.73) from be984f to E5E674
|
| First transfer of NFTs (#5) |
bd0f24
|
0xbd0f24d0bb94445946172ba6318c59e05e4ae010c88c11004c11bc4895a59fb4
|
See below ... |
be984f : TX hash 94c089 : from victim → to E5E674be984f : TX hash 0b2c82 : from victim → to E5E674be984f : TX hash 7909c0 : from victim → to E5E674be984f : TX hash b22baf : from victim → ...
4.15 ETH : Input data: 0x : → to E5E674
Note: This is a basic transfer with no input data. This normally should imply that the TX was sent voluntarily. If this occurs in such fashion, typically one would assume that the victim has had their private key or seed phrase compromised. As you will note, given the extremely common nature of this occurrence, this cannot be the case.
be984f : TX hash bd0f24 : from victim → ...
be984f → to E5E674 → ...
ForgedToken (FT) ...
16364, 4135 ... - Transfer of 5x Fortune Frie... (FFC) ...
To answer this can either examine the Logs on Etherscan, or use a more powerful lens.
Using a tool called Heimdall, we will examine the call data of the next transaction; first, we look at Etherscan at the superficial details of the transaction. This is the OpenSea: Seaport transaction where the CloneX NFTs are stolen. Notice the details we are presented:
Sale: 3 NFTs For 0 Ether on OpenSea
Transfer of CloneX (Clonex) From
0xbe984f5d3D6040d57fFc8d7700243E29dA6750b7 (Victim; see 'Transaction Action')
0x0000098a312e1244f313f83cac319603a97f4582 (Literally 'From:' - address rightly labeled Fake Phishing)
0x00000000006c3852cbef3e08e8df289169ede581 ('Interacted With (To):' - Seaport 1.1)The full output is far too long to include in this document, and unlikely to be interesting to most readers, so we will only include the important details.
$ ❯ heimdall decode 0x0ba3374d64dfd63ee3c5df4a1be72d93a68d649efca2f2e6f45799ad7c2f36a1 -d
warn: couldn't find any matches for the given function signature.
trace:
[220] heimdall::decode(0x0ba3374d64dfd63ee3c5df4a1be72d93a68d649efca2f2e6f45799ad7c2f36a1)
│
├─ selector: 0xa8174404
├─ calldata: 2660 bytes
│
├─ input 0: 0000000000000000000000000000000000000000000000000000000000000040
│ 1: 00000000000000000000000000000000000000000000000000000000000006e0
│ 2: 0000000000000000000000000000000000000000000000000000000000000001
│ 3: 0000000000000000000000000000000000000000000000000000000000000020
│ 4: 0000000000000000000000000000000000000000000000000000000000000040
│ 5: 0000000000000000000000000000000000000000000000000000000000000600
│ 6: 000000000000000000000000be984f5d3d6040d57ffc8d7700243e29da6750b7
│ 7: 000000000000000000000000004c00500000ad104d7dbd00e3ae0a5c00560c00
│ 8: 0000000000000000000000000000000000000000000000000000000000000160
│ 9: 0000000000000000000000000000000000000000000000000000000000000360
│ 10: 0000000000000000000000000000000000000000000000000000000000000000
│ 11: 00000000000000000000000000000000000000000000000000000000630ceaec
│ ...
│ 82: 0000000000000000000000000000000000000000000000000000000000000002
└─ ← ()Eventually we end up with 82 lines; within them, we can manually pick-apart the data to extract 40 char. long addresses. We end up with this:
selector: 0xa8174404
6. be984f5d3d6040d57ffc8d7700243e29da6750b7 | Victim
7. 004c00500000ad104d7dbd00e3ae0a5c00560c00 | OpenSea: Pausable Zone
19. 49cf6f5d44e70224e2e23fdcdd2c053f30ada28b | CloneX contract
24. 49cf6f5d44e70224e2e23fdcdd2c053f30ada28b | .
29. 49cf6f5d44e70224e2e23fdcdd2c053f30ada28b | .
35. 49cf6f5d44e70224e2e23fdcdd2c053f30ada28b | .
39. f63cd470da56c990cd41409113a1524348c5cc88 | <- Drainer recv. here |
-> hop to Polygon to find `0xd6c67687` function signature, coincidentially discovered earlier (not featured above)
-> contract: address/0x1d8c14ebdaea565b9a0723a5ce4b01bbdf80a27b : [ ETH / POLYGON ]
-> the title of this document is finally relevant: examine this contract on Polygon :
-> https://polygonscan.com/address/0x1d8c14ebdaea565b9a0723a5ce4b01bbdf80a27b an 1155
-> ... an 1155 with an enmorous amount of `Safe Transfer From` function calls ...
41. 49cf6f5d44e70224e2e23fdcdd2c053f30ada28b | CloneX contract
45. f63cd470da56c990cd41409113a1524348c5cc88 | <- Drainer recv.
47. 49cf6f5d44e70224e2e23fdcdd2c053f30ada28b | Clonex contract
51. f63cd470da56c990cd41409113a1524348c5cc88 | <- Drainer recv.Here is where we will stop for the time being. We hope that this has at least begun to help readers in understanding some of what is transpiring, though we have yet to offer an answer to how exactly these draining transactions are transferring the NFTs (or for that matter: also ERC20s, ERC1155s, and even plain ETH). We only have so little time to explain each item, and much of any further information may either be speculative, or possibly critical to investigative efforts.
It's important that we take note of the ongoing situation. This is not a one-off situation.
One reason for breaking our silence now, rather than waiting and only coming forward when we feel that the explanation is whole, is due to the fact that we see this happening every single day. We hope that by speaking up we can bring light to a situation that is otherwise going largely unobserved.
We will annotate or label them below.
We are not nearly as strong divided as we are united against this. There are many brilliant minds who have yet to offer insight - though we also would assert that there is a lot more of that kind of activity happening quietly in the shadows; it's ultimately not a reassurance if we do not speak it.
ps. Shadowfury is a way better LARP than 'federalagent' : get rekt monkey-drainer boy - From Belgium / SFS
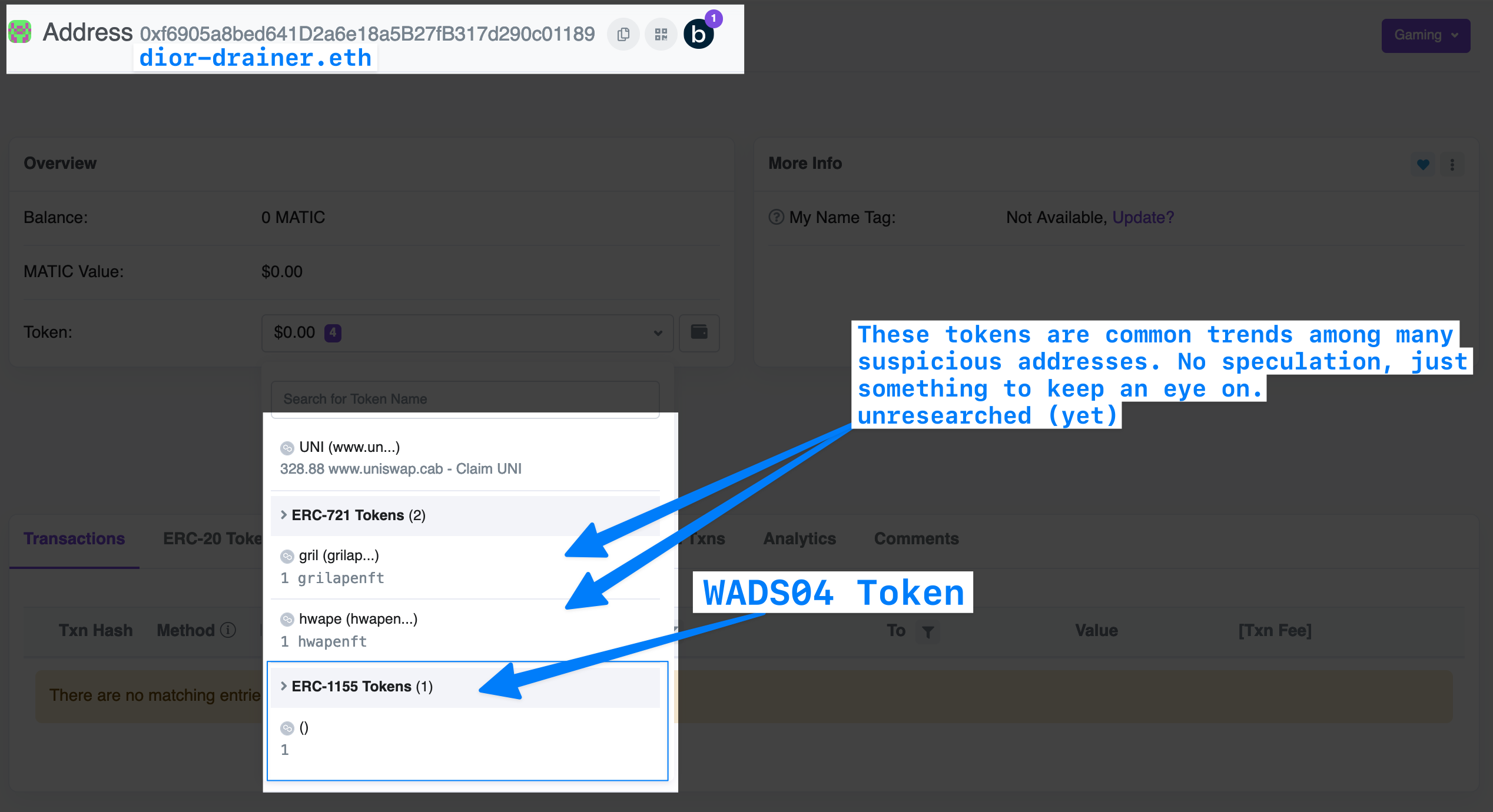
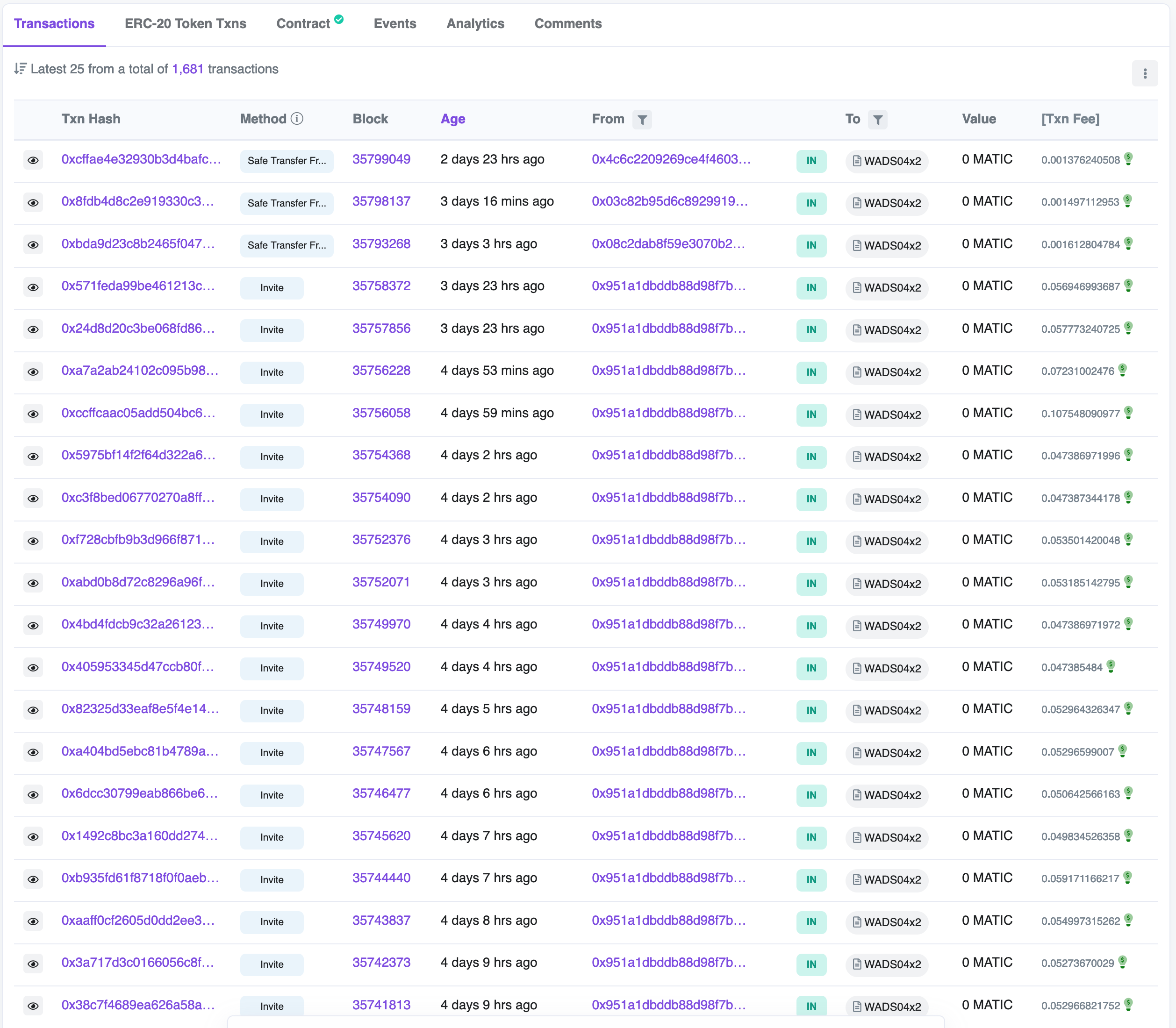
59 addresses discovered in the past 24hrs. (there are 60 now...) / matching source code for the 1155s on Polygon:
Here are the 'WADS04' contracts, to start. We are still examining these. They just popped up today, and just seem like dust attacks at first glance.
WADS04x1: 0xda78892a923591771a7d5f9027c6da9762fd9512
WADS04x2: 0xc64174e79cda9312e770d8de5bd5670156855657
WADS04x3: 0x462db9fafbf9a93ee93e0bffdd70bc047476aa25
WADS04x4: 0x0e66c2746a068ee7495844aa2e3f7ab67c20b58a
--- 1155 clones ----------------------------
- 0x6365cbca57ba69bf18bec0d63d4fe7463185d69a
- 0xfc21fb65120a09082b5bffd63292776940c5a943
- 0x30f17426c7e4294a13152075f92f863639e97e71
- 0x583ec37327c90724fc56bf9dff310b28cbd8a017
- 0x8bb773d194ecacc6d5e05ed969ef48b68beec841
- 0x1257f7e3f66ae8541d8f9dc2de95c004bd67258c
- 0x7168d1b290b866c65c56feb6786f3b876870292a
- 0x7728c7e142664a827b75fe4df6d15f75870fa64a
- 0x5369f46c85723d7440700252e35ee24c1054b082
- 0xc4091df73ac206ace1424e6ba416b2df54ad17ba
- 0xc4985e382cff6dad7b8c0ab61511759127de3c9c
- 0x89c858427cce7f9737a2e7d0ae81ad9c39334415
- 0xc90cbd562a3b65f7dd99f4c4fb92d308fb82af1c
- 0xe0f73fedb2b75b69f1b7e48e2174dfc9f1a55ba4
- 0x90447e648d7500dd7ce8fedfc10c87f2e641a21d
- 0x93d761db19e857e000feb9bf0ff355318421fbb5
- 0x188c42de1c7e70c491816613a192e2628b7111d7
- 0x816e12be4cc24dfed6838e18f93864610273fd78
- 0x43b141078a263ffd7080bcc370eaafdc8a5f57a4
- 0x61d0e8dba3a762dbed60c36da3be4d5d067153fd
- 0x9ec3ce1b361755bdc056af6df65b8a468ed638e5
- 0xfd950f26c6353551bbfe4ef951cce7f95b85d3d5
- 0x5b031f7ab414a896fcf0cb1cb11ac33621c364db
- 0x9292346329cfad84e4545c557a32849355a49d91
- 0x39f92cac0841bc22307dac7f4245adaed9e97c3e
- 0x4a2f6568f5d289def55189ea2f4fd777357c2c78
- 0xc8f255aa88f9b7a2e85b7d7ea358e07b5f75beb5
- 0x3d02591faa79c702575b3da58d3e58d2ac4159cd
- 0x31c00b2077af1572b6df984423cbda045472704b
- 0x0a78e15143f577fb9484ff0a3c4bdaa4195019e3
- 0xf7186a13b5aac4a7d8a77f1d9065b33a11a524cd
- 0xb2d2ad2345e09948c2792a2f7da69186531e8bc7
- 0x9803252c3768fa5ac23306a42c033fe3348a64e6
- 0x7a4b50a0023fc275cb2dbe71636894a505998d28
- 0x7945a7dead451f77a8c99227c838865710ba6bf1
- 0xa4457c2028c64c9f1713919a9cbf4be7280e52f8
- 0x858995a2604a3a8c8d42e5b765770edf8f43c03a
- 0xaf1a68d4c1e2b93cca243774ae90042f99023566
- 0x074b71605c4540c8526d6ba414e267d3415ab3c7
- 0x17f96a9835fe4c494e132a31fed5355d56391e7d
- 0x4027cdc3b05e9f50dd1840a4332bfe4ff0692959
- 0x1f2ecc7d962796805c65878e46b09d58fdb8db38
- 0x744d2ef110004794d76a75b58853443ad9241faf
- 0xc56ac0ac81748c3d7b407e6e7fd613de3d5f95b2
- 0x8a59e32a036edef2dcd0c3ae1ea0030f97524cff
- 0x3b6009d922536e6a127dba2863a7d23129cf9cd8
- 0xd3b73cd02a5009ee0c83f785590c4dede2cf1f93
- 0x4433a08e16c44ed468e87cccbf9c7fc780729d4c
- 0x5bbf71ea2dd25784fd027ee91eb2b4d233e1c7ca
- 0x877581e1df1564873a11976e52e6f6de3097442d
- 0xbcec0ca8aae2a229fbb29798e6ab4b74b132c2ca
- 0x7f4f31ec7e3bc1886f734a13d541cb61fd693e52
- 0x9bac79ff1d9e627419d2e59232c3e376d02428b1
- 0xa476372f42aa60a3cd280c9ab3d180418c054f65
- 0xf248d361d1580fc87e10de29fdfa7d462277dd97
- 0xf8055b852776699ce235662e83ac2b6a249d2112
- 0xb9b87d9be1094a6e4a1c7af58d55bf7e66b22a74
- 0x90bcd98dcf9749baedb4140c1b21c932bf3ed309
- 0x51c251ccfdaea4010eefc621160873dcc5fae8e2
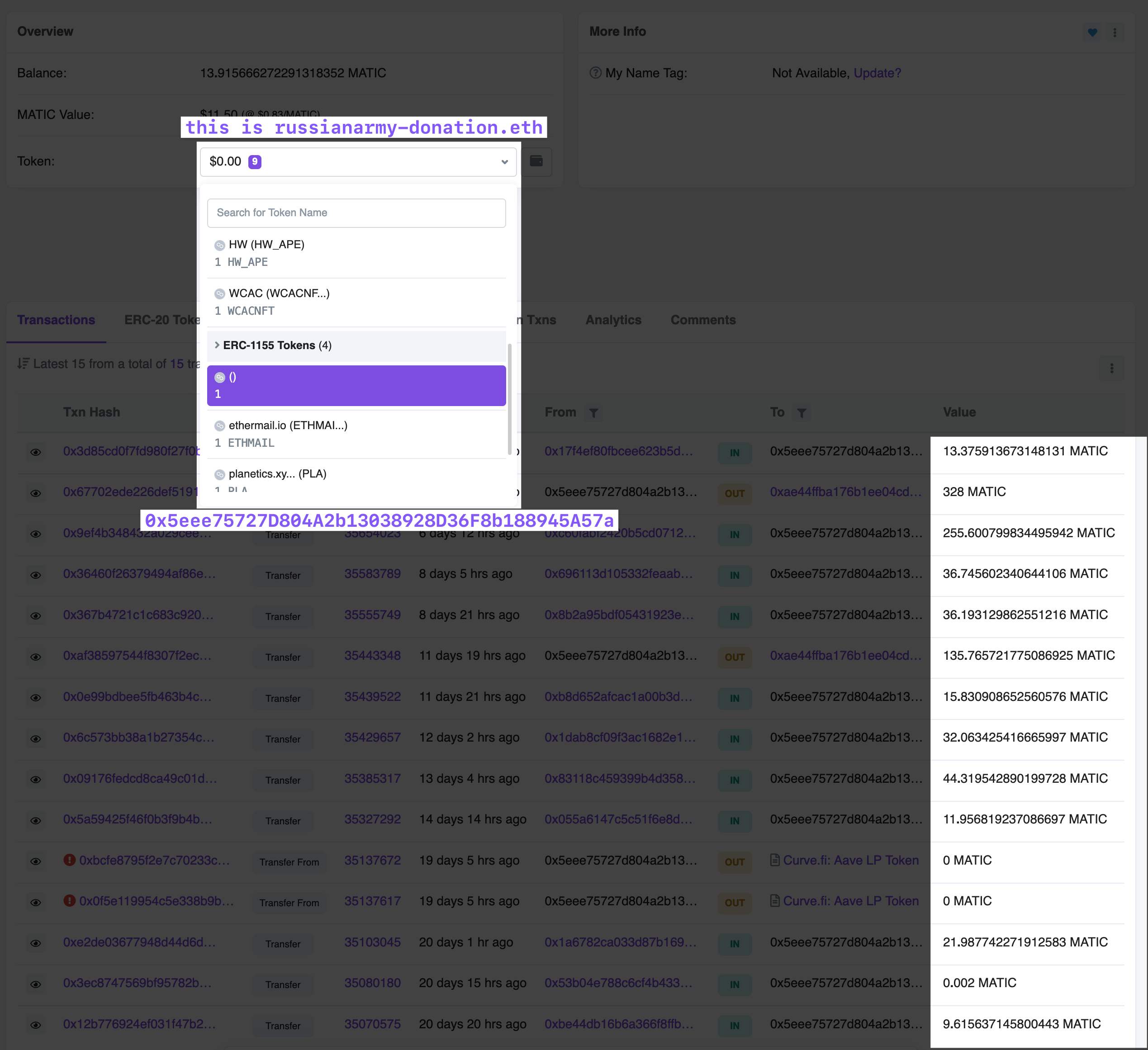
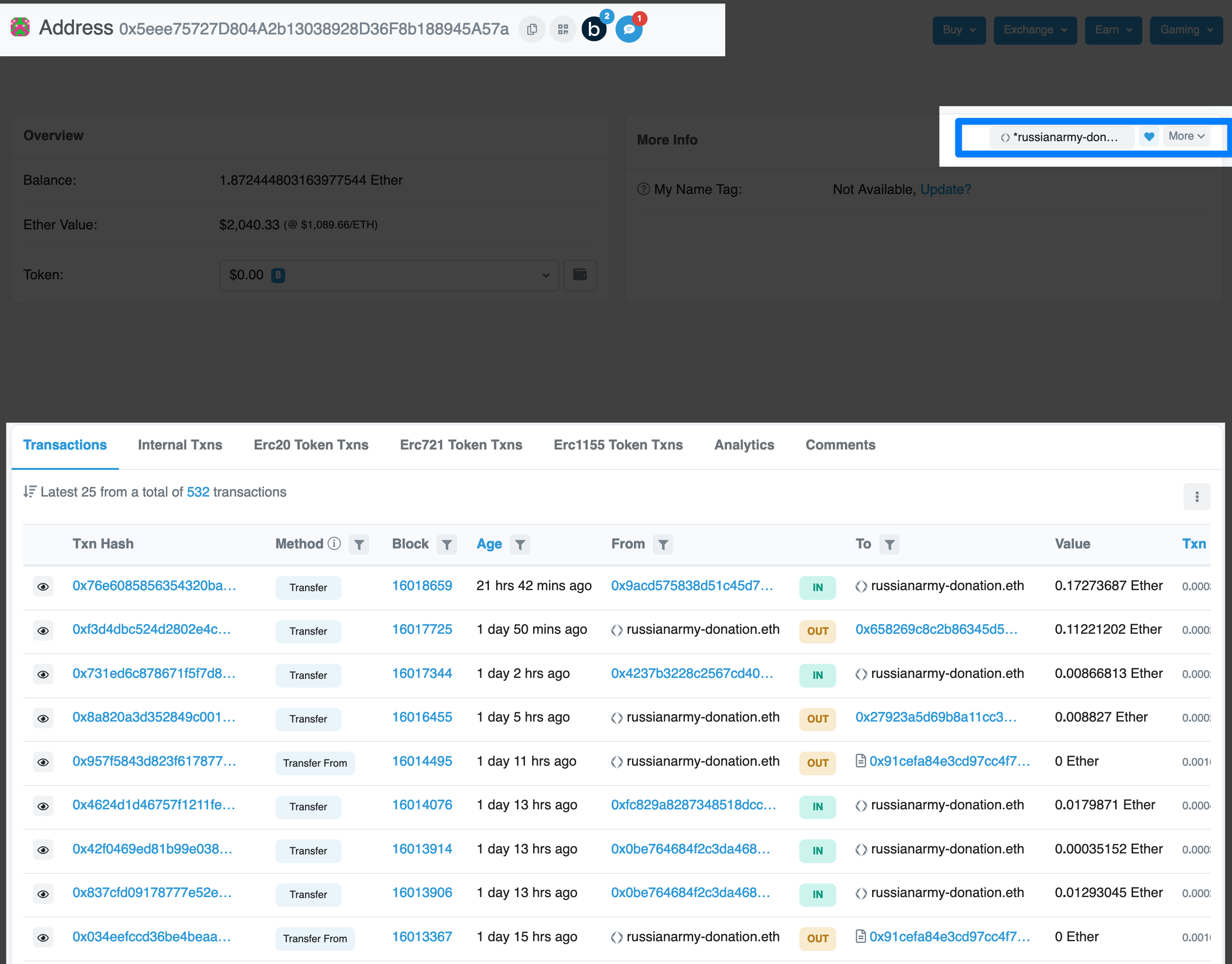
monkey-drainer.eth & related address, with screenshots:
Various, since about September, give or take a few weeks.
0x2191fD88F246B74CEA560356177DDED054c43F27 MD-EOA-RECV-001
0x52B1280d451D60AB4481C83944Dd4eE94061a870 MD-CONTRACT-001
0x59148312BF9AC8f890Ee3CaEE19D8490E07c045b MD-EOA-EXIT-001
0x0e6CcF10c74655cdC5a96953D4B8116Ab3D9252c MD-EOA-RECV-002
0xd13b093EAfA3878De27183388Fea7D0D2B0AbF9E MD-C-SecurUpdates <- This one is on ::11:: chains
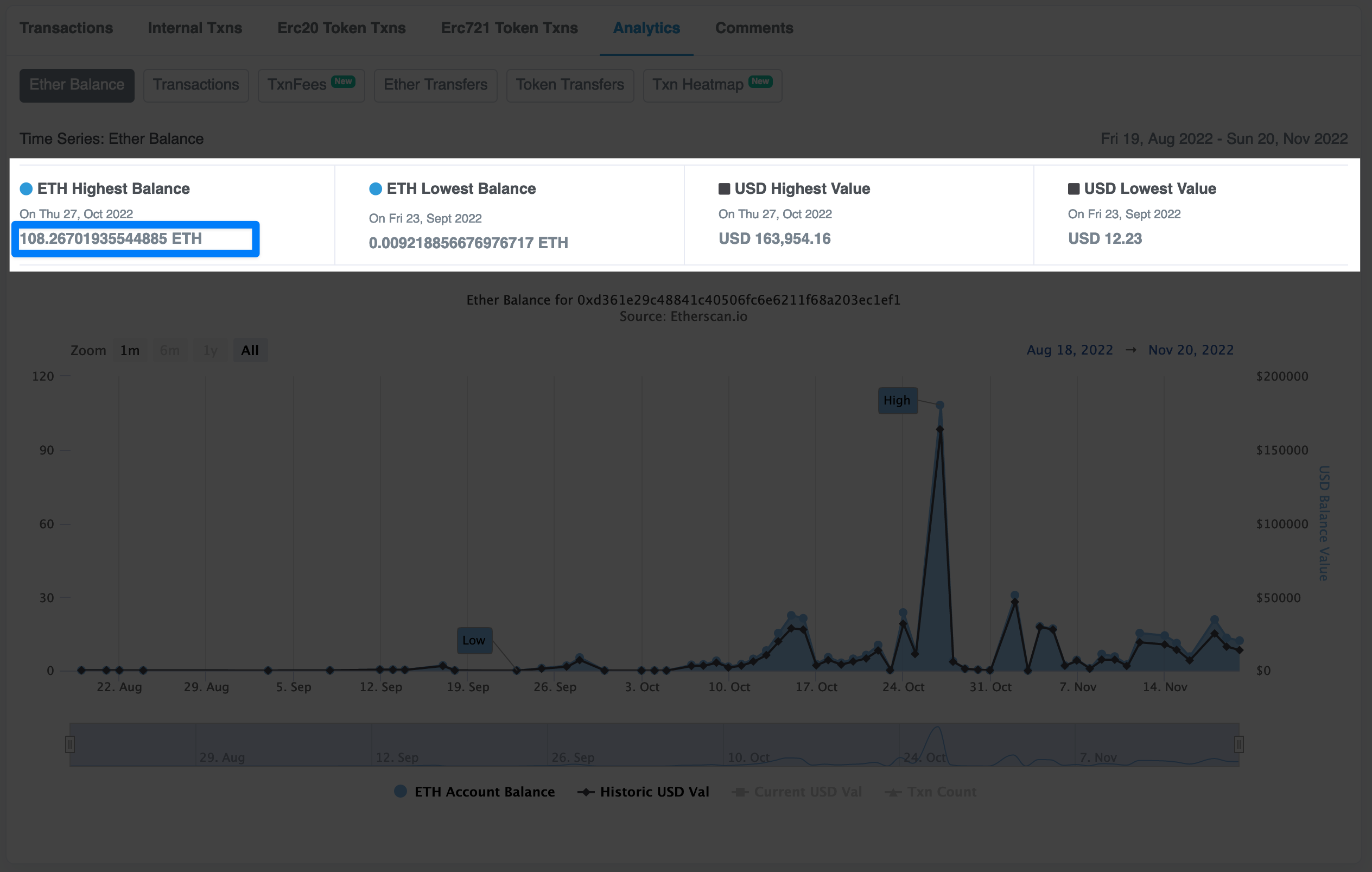
0xD361e29C48841C40506FC6E6211f68a203Ec1Ef1 MD-SecUpDEPLOYER <- lots of federalagent/tornado cash
0x67d102bbe24Bc144F566CB0562c8F53feea7b92d MD-EOA-EXIT-002
0x9FC8265F2b376084423A1A348a89Ecd894a9d106 MD-Monkey-Drainer
0xAf6FDAc3A733c14F0bDdE319A931fa80E05F0696 MD-EOA-UNLABEL-1
0xCE7CB10938fD6d379Cfaf26D75A0dB0A9642159b MD-EOA-UNLABEL-2
0x1524d8bEfC59c85b19858f9Ba5F3955E8d0D0F14 MD-EOA-UNLABEL-3
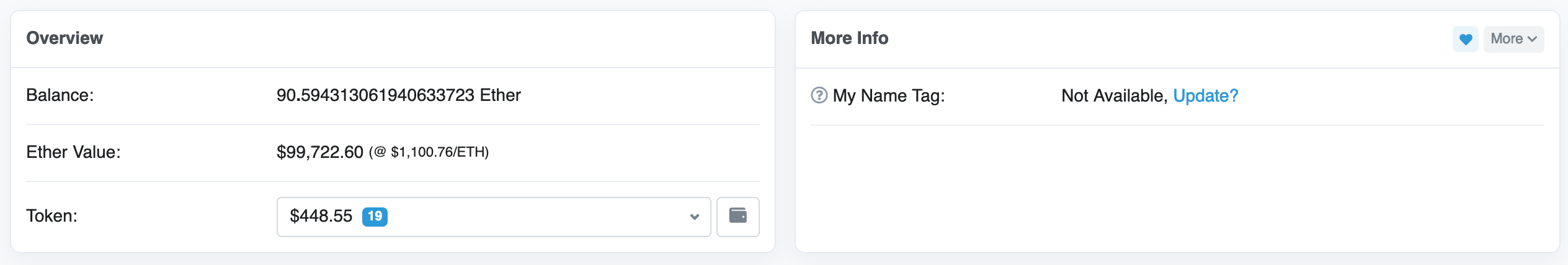
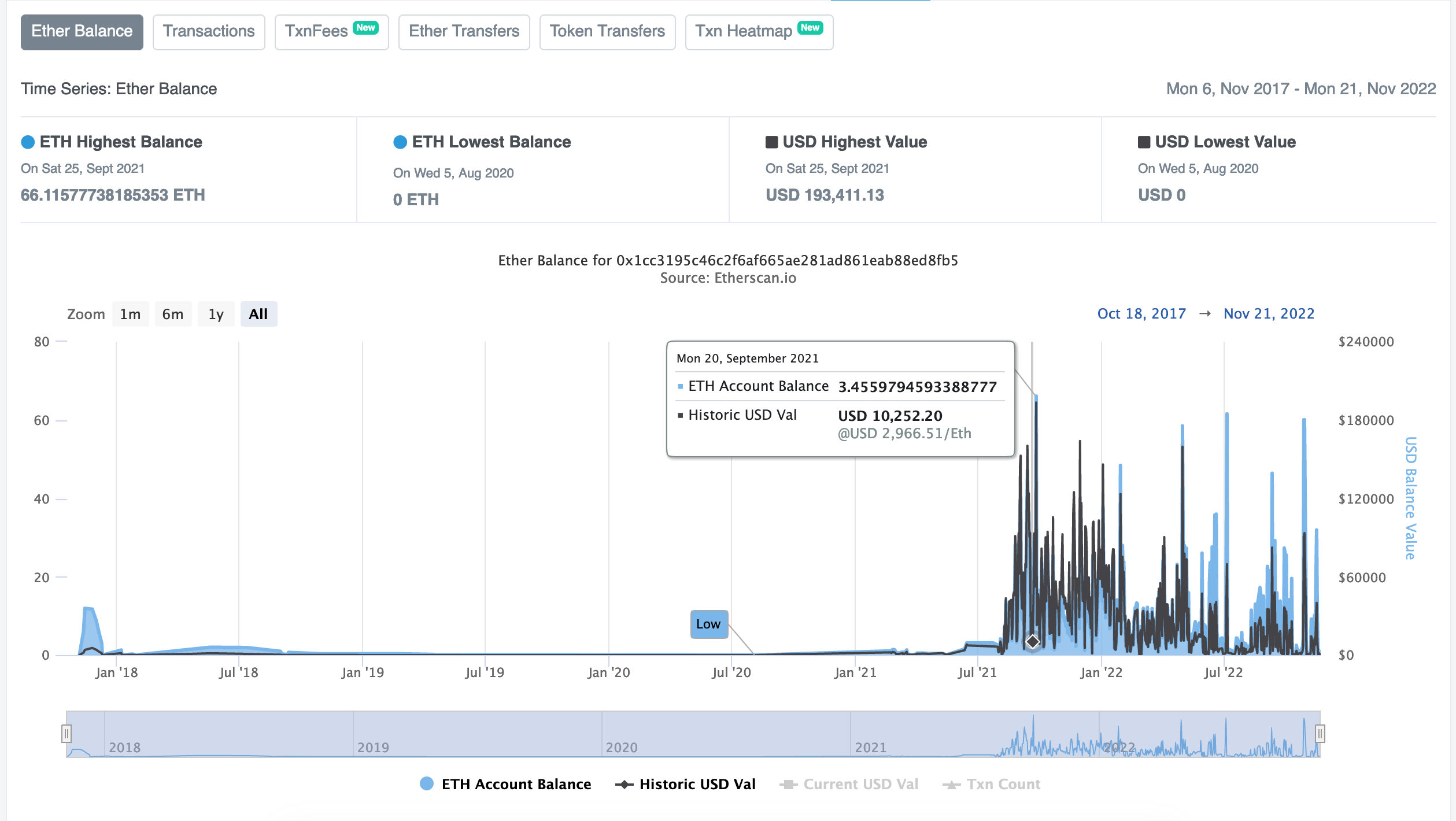
0x1cC3195C46C2F6AF665Ae281ad861eAb88ed8Fb5 MD-Pokgai.eth <- becme the most active for a while ~1mo ago
0x0000098a312E1244f313F83CAc319603A97F4582 MD-EOA-UNLABEL-4
0xC8Bd8a024D829CB2cb29D28EFd463Fe010d58c17 MD-EOA-UNLABEL-5
0x588aDaF721A828aa3d369E04EA9a107Ca85C2e74 MD-EOA-RECV-003 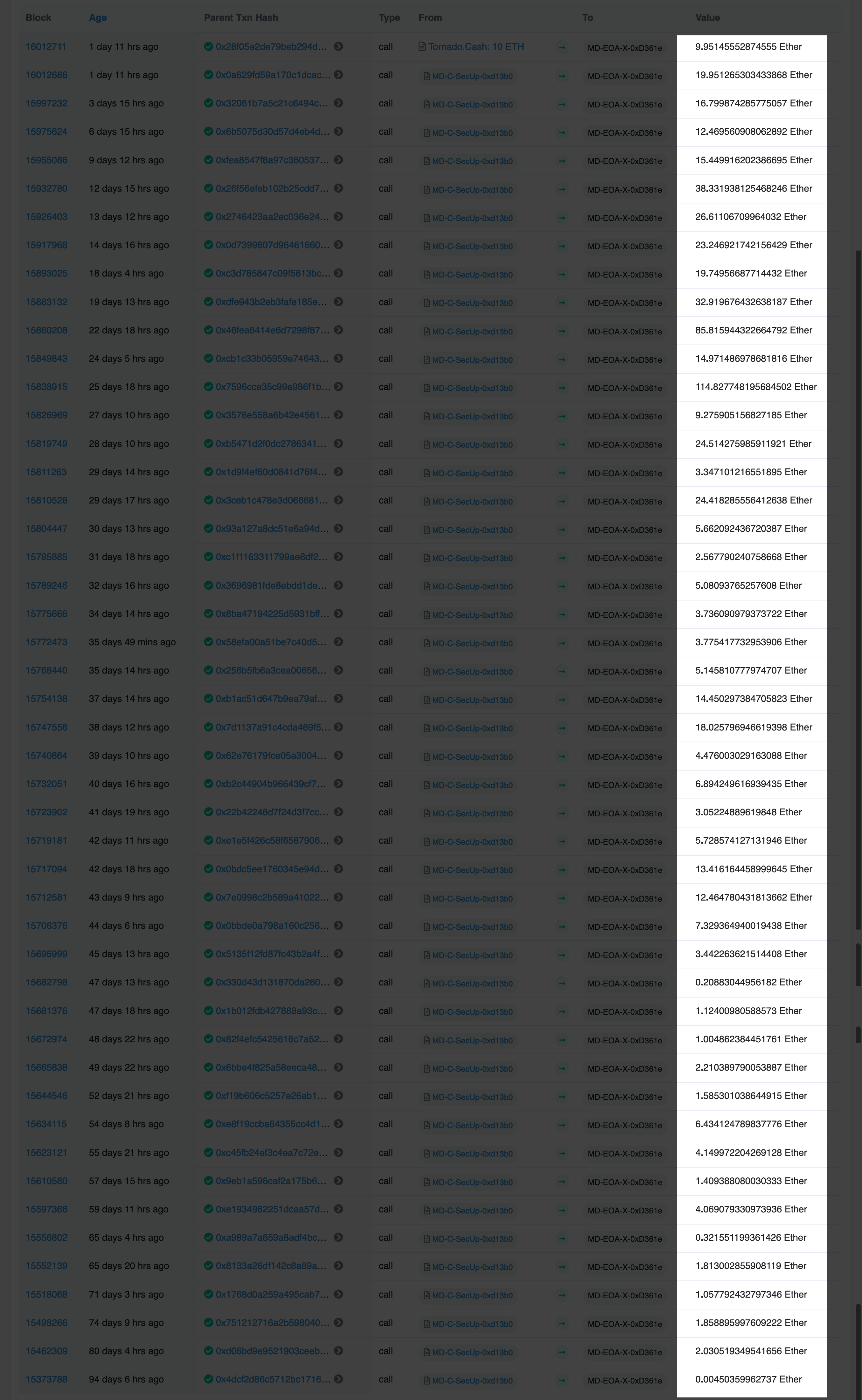
https://etherscan.io/address/0x84527b5949d479c879b8dd71cd8f79048cdf6fb8
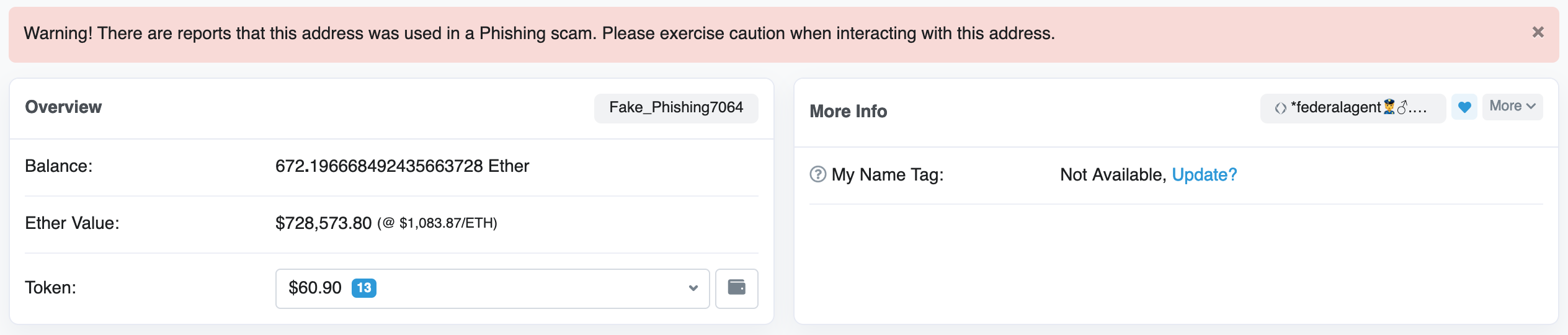
https://etherscan.io/address/0x1524d8befc59c85b19858f9ba5f3955e8d0d0f14